Best Practices for Developing Secure and Compliant FinTech Applications

In the past year alone, data breaches at major FinTech companies have exposed millions of user records, highlighting the critical need for efficient security measures in this fast-growing industry. As consumers increasingly adopt digital financial services – from mobile payments to online investing – from mobile payments to online investing – the volume of sensitive data entrusted to FinTech applications continues to rise. However, this greater convenience came with heightened security risks.
Building trust with users is crucial for FinTech companies. Financial information is inherently personal and requires the utmost protection. By prioritizing security from the very beginning, FinTech companies can create a safe and reliable environment for users, driving the long-term success of their innovative solutions. So how to build a FinTech app that is secure and compliant? This article outlines the best practices for developing secure and compliant fintech solutions.
Building a Security-First Culture
Watertight security isn’t achieved through technical measures alone. Cultivating a development environment where security is a top priority for everyone involved is the foundation of a truly secure fintech application. This ‘security-first’ culture encourages a shared responsibility for protecting sensitive data and protecting user privacy. Here’s how to cultivate this essential mindset.
Security Champions
The implementation of a Security Champion program is one of the most effective ways to promote a security-first culture within a fintech organization. Security champions are individuals within the development team who act as liaisons between the security and engineering departments, promoting security-best practices and raising awareness among their peers.
Security champions play a crucial role in evangelizing security best practices, contributing to security standards, and conducting threat modeling and secure code reviews. They serve as a bridge between the security team and the fintech developers, promoting collaboration and making sure that security considerations are integrated into every aspect of the software development lifecycle (SDLC). By establishing a network of security champions, fintech companies can create a culture of security that permeates throughout the organization, from the executive suite to the engineering trenches.
Security Awareness Training
Alongside, implementing a Security Champion program, fintech companies must invest in comprehensive training programs that cover the latest security threats, best practices, and regulatory requirements. By equipping developers with the knowledge and skills necessary to identify and mitigate security risks, fintech companies can empower their teams to make informed decisions and take proactive measures to protect sensitive financial data and systems.
Security awareness training should be customized to the specific needs and challenges faced by FinTech organizations, addressing topics such as secure coding practices, data encryption, identity and access management, and incident response planning. By making security training a continuous and mandatory part of the development process, FinTech companies can make sure that their teams remain vigilant and adaptable in the face of growing security threats.
Secure Coding Practices for FinTech Apps
Building a security-first culture goes hand-in-hand with implementing secure coding practices. These practices act as a developer's toolkit for writing code that is resistant to common attacks and vulnerabilities.
Industry Standards as Your Guide
A prominent resource in this area is the OWASP Top 10, a list of the most critical web application security risks. Integrating these well-documented vulnerabilities into your development process allows you to proactively address potential weaknesses. By understanding these common threats, developers can write code with security in mind from the very beginning.
FinTech-Specific Vulnerabilities
- SQL Injection
FinTech solutions often rely on user input to process transactions and access financial data. Improperly handling this input can leave your application susceptible to SQL injection attacks, where malicious code is injected into database queries, allowing attackers to steal or manipulate sensitive information.
- Broken Authentication
Weak authentication mechanisms often lead to unauthorized access. FinTech applications should enforce strong password policies, utilize multi-factor authentication (MFA), and avoid storing passwords in plain text.
Early Detection
- Static Code Analysis (SCA) and Vulnerability Scanning
These automated tools can be invaluable in identifying security flaws early in the development lifecycle. Static code analysis tools such as Snyk Code can scan the source code for common security flaws and provide actionable insights to developers. By integrating these tools in their CI/CD pipelines, FinTech companies can catch security issues early and make sure that vulnerabilities are not introduced into production environments.
Putting Secure Coding into Practice
Secure coding practices in FinTech software development services should also include practical examples of secure coding techniques. For instance, when handling user input, developers should always validate and sanitize the input to prevent injection attacks. This can be achieved by using parameterized queries or prepared statements when interacting with databases. Furthermore, developers should follow best practices for password storage, such as using secure hashing algorithms and salting techniques to protect against brute-force attacks and credential stuffing.
Robust Authentication and Authorization
Verifying a user's identity and controlling access to sensitive data are fundamental aspects of FinTech security. When it comes to web apps or mobile app development services in FinTech, robust authentication and authorization mechanisms act as gatekeepers so that only authorized users can access specific features and functionalities within your application.
Multi-Factor Authentication (MFA)
One of the most effective security measures for FinTech applications is the implementation of multi-factor authentication (MFA). MFA requires users to present two or more pieces of evidence, or factors, to verify their identity before gaining access to sensitive information or performing critical actions. This approach considerably reduces the risk of successful attacks, as it is much more difficult for attackers to compromise multiple authentication factors simultaneously.
FinTech Companies can utilize a variety of MFA factors, including knowledge-based factors (e.g. passwords, PINs), possession-based factors (e.g. one-time codes, security tokens), and inherence-based factors (e.g. biometrics like fingerprints, facial recognition). By combining these factors, FinTech applications can provide a strong, layered defense against unauthorized access. This makes sure that only legitimate users can interact with the system.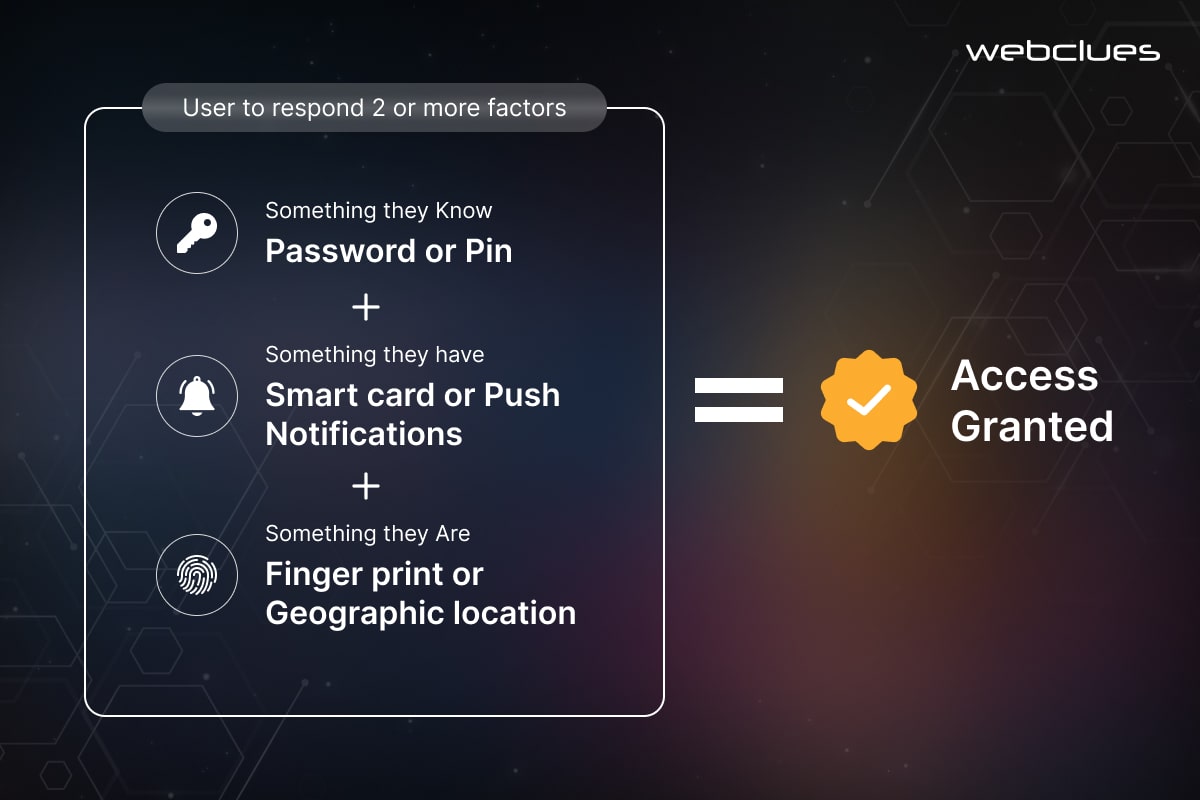
Biometric Authentication
Biometric authentication is gaining traction in the FinTech industry as a secure and convenient method of user verification. Utilizing unique physical or behavioral characteristics, such as fingerprints, facial features, or voice patterns, biometric authentication provides a high level of assurance that the user is who they claim to be. This technology can improve security considerably by making it much more difficult for attackers to impersonate legitimate users.
Moreover, biometric authentication also offers a more hassle-free user experience, as it eliminates the need for traditional password-based authentication. This can lead to increased customer satisfaction and reduced friction in the user’s interactions with FinTech applications.
Principle of Least Privilege
The principle of least privilege dictates that each user, process, or system should only be granted the minimum permissions necessary to perform their intended tasks. For example, a customer service representative might only need access to view account information, while a financial analyst might require additional permissions to modify investment portfolios. By adhering to this principle, FinTech companies can notably reduce the potential impact of a security breach or compromised identity. If an attacker gains access to a user account or system, the damage they can inflict is limited to the specific permissions granted to that entity, rather than allowing them to escalate privileges and gain unrestricted access to sensitive data or critical systems.
Role-Based Access Control
To effectively implement the principle of privilege, FinTech companies can utilize role-based access control (RBAC) mechanisms. RBAC is a security framework that assigns permissions to users based on their roles and responsibilities within the organization. By defining and managing user roles, FinTech companies can make sure that each individual has access only to the resources and functionalities they require to perform the job duties.
RBAC provides a structured and scalable approach to access management, allowing FinTech companies to easily onboard new users, update permissions as roles change, and maintain a clear audit trail of user activities. This level of control and visibility is crucial for maintaining compliance with industry regulations and mitigating the risk of unauthorized access or data breaches.
Securing Data Storage and Transmission
FinTech applications handle large amounts of sensitive user data, from account numbers and transaction history to financial holdings. Safeguarding this data requires a multi-layered approach that secures it both at rest (on servers) and in transit (during communication).
Data Encryption at Rest and In Transit
Encryption is a fundamental security measure for protecting sensitive data in the FinTech ecosystem. FinTech companies must encrypt the data - both at rest, when stored on servers and databases, and in transit, during communication between various components of the application and with external systems.
By encrypting data at rest, FinTech organizations can protect their sensitive information, such as customer financial records, transaction histories, and personal identifiable information (PII), from unauthorized access, even in the event of a data breach. Commonly used encryption algorithms for data at rest include AES (Advanced Encryption Standard) and RSA (Rivest-Shamir-Adleman).
Similarly, encrypting data in transit is crucial to protecting the confidentiality and integrity of information as it moves between the FinTech application, user devices, and external systems. Secure communication protocols, such as HTTPS, SSL/TLS, and FTPS, should be employed to protect sensitive from eavesdropping and man-in-the-middle attacks during transmission.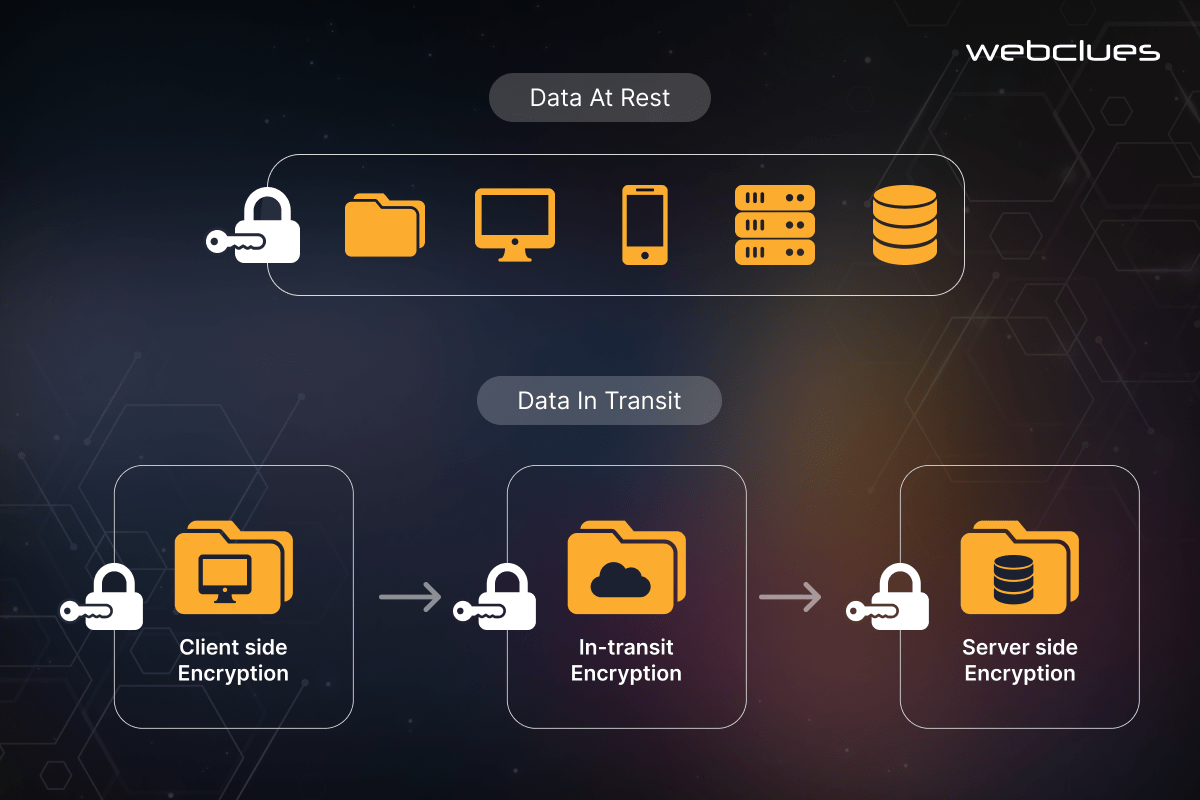
Key Management Strategies
Effective key management is a critical component of any encryption-based security strategy. FinTech companies must implement efficient key management practices to ensure the confidentiality and integrity of their encryption keys, which are the foundation for protecting sensitive data.
This includes securely storing encryption keys, regularly rotating them, and carefully controlling access to key management systems. FinTech organizations should also consider using hardware security modules (HSMs) or cloud-based key management services to improve the security and scalability of their key management infrastructure.
Data Loss Prevention (DLP)
In addition to encryption, FinTech companies should implement comprehensive data loss prevention (DLP) measures to reduce the risk of accidental or unauthorized data leaks. DLP tools can monitor and control the flow of sensitive information, both within the organization and across the network, to prevent it from being shared or transmitted outside of authorized channels.
DLP solutions can be configured to detect and block the transfer of sensitive data, such as customer financial information or trade secrets, through various channels, including email, cloud storage, and removable media. By implementing DLP, FinTech companies can improve their overall data security posture and maintain compliance with industry regulations such as PCI DSS and CDPR.
Secure Cloud Storage Considerations
As FinTech companies increasingly utilize cloud-based services for data storage and processing, it is essential to carefully evaluate the security measures provided by cloud service producers. FinTech organizations should make sure that their cloud storage solutions offer robust encryption, access controls, and logging capabilities to protect sensitive data from unauthorized access and maintain regulatory compliance.
Furthermore, FinTech companies should consider implementing their own encryption and key management strategies, even when using cloud-based storage, to maintain control over the security of their data and reduce reliance on the cloud provider’s security measures alone.
Building Trust Through Compliance
The FinTech industry operates within a complex regulatory environment, with a myriad of compliance requirements that must be carefully addressed to maintain the security and integrity of financial services. It is crucial for FinTech companies to actively identify the relevant regulations, integrate compliance considerations throughout the software development lifecycle, and effectively manage the risks posed by third-party vendors.
Identifying Relevant Regulations
FinTech companies must stay abreast of the key regulations that govern their operations and the handling of sensitive financial data. Some of the most prominent regulations include:
- PCI DSS (Payment Card Industry Data Security Standard): Mandates security requirements for organizations that handle credit card payments.
- GDPR (General Data Protection Regulation): Establishes data privacy and security standards for the processing of personal data within the European Union.
- AML (Anti-Money Laundering) and KYC (Know Your Customer) Regulations: Require FinTech companies to implement measures to prevent financial crimes and verify the identity of their customers.
- CCPA (California Consumer Privacy Act): Grants California residents certain rights over their personal information and imposes compliance obligations on businesses.
By thoroughly understanding the applicable regulations, FinTech companies can develop a comprehensive compliance strategy that addresses the specific requirements and risks associated with their products and services.
Compliance Integration in the Development Lifecycle
Ensuring compliance must be integrated into every stage of the software development lifecycle. This approach, often referred to as “Compliance-Driven Development,” involves incorporating compliance considerations from the initial planning and design phases, through implementation, testing, and deployment.
FinTech companies should establish clear compliance requirements, policies, and processes, and embed them into their agile development methodologies. This may include conducting regular risk assessments, implementing secure coding practices, and automating compliance checks within the CI/CD pipeline. By making compliance a core part of the development process, FinTech organizations can proactively identify and mitigate potential compliance risks, reducing the likelihood of costly breaches or regulatory penalties.
Third-Party Vendor Risk Management
FinTech applications often rely on a complex ecosystem of third-party vendors, such as cloud service providers, payment processors, and data analytics platforms. Assessing and managing the security posture of these third-party vendors is crucial, as a breach or compliance failure within a third-party service can have significant consequences for the FinTech company and its customers.
FinTech organizations should implement an effective third-party risk management program that includes due diligence assessments, ongoing monitoring, and clear contractual agreements that outline security and compliance requirements. This may involve evaluating the vendor's security controls, incident response plans, and compliance certifications, as well as conducting regular audits and penetration testing so that third-party services meet the FinTech company's security and compliance standards.
Continuous Security Monitoring and Improvement
Building a secure FinTech application is just the first step. The incessantly growing threat landscape requires continuous monitoring and improvement to maintain a strong security posture.
Security Testing and Penetration Testing
Regular security testing and penetration testing are essential components of a comprehensive security strategy for FinTech applications. These assessments help FinTech companies identify and address vulnerabilities before they can be exploited by malicious actors.
Security testing involves the systematic examination of the FinTech application's security controls, including access management, encryption, and input validation. By conducting comprehensive security testing, FinTech companies can uncover potential weaknesses and make sure that their applications meet industry-recognized security standards, such as the OWASP Top 10.
Incident Response Planning
In the event of a security breach or incident, having a well-defined incident response plan is crucial for FinTech companies. This plan outlines the steps to be taken to identify, contain, eradicate, and recover from the incident, minimizing the impact on the organization and its customers.
The incident response plan should include clear roles and responsibilities for the incident response team, communication protocols, and procedures for notifying relevant stakeholders, including regulatory authorities and affected customers. Regular testing and updating of the incident response plan allows the FinTech company to be prepared to respond effectively to a wide range of security incidents.
Conclusion
User trust is vital when it comes to the FinTech Industry. By prioritizing secure and compliant development practices, FinTech companies can build a strong foundation for user confidence. This not only protects sensitive financial data but also cultivates an environment that encourages innovation and growth within the industry.
From cultivating a security-first culture to implementing robust authentication and data encryption, the practices outlined in this blog create a multi-layered defense against cyber threats.
At WebClues Infotech, we are experts in secure FinTech development. We offer a comprehensive suite of solutions and services to help you build applications that prioritize user security and data privacy.
Build Your Agile Team
Hire Skilled Developer From Us
Stop security breaches and build secure FinTech apps with WebClues
Don't let security vulnerabilities threaten your FinTech app. Partner with WebClues to implement best practices and build a secure, user-trusted solution.
Get a Quote!Our Recent Blogs
Sharing knowledge helps us grow, stay motivated and stay on-track with frontier technological and design concepts. Developers and business innovators, customers and employees - our events are all about you.
Contact
Information
India
Ahmedabad
1007-1010, Signature-1,
S.G.Highway, Makarba,
Ahmedabad, Gujarat - 380051
Rajkot
1308 - The Spire, 150 Feet Ring Rd,
Manharpura 1, Madhapar,
Rajkot, Gujarat - 360007
UAE
Dubai
Dubai Silicon Oasis, DDP,
Building A1, Dubai, UAE
USA
Atlanta
6851 Roswell Rd 2nd Floor,
Atlanta, GA, USA 30328
New Jersey
513 Baldwin Ave, Jersey City,
NJ 07306, USA
California
4701 Patrick Henry Dr. Building
26 Santa Clara, California 95054
Australia
Queensland
120 Highgate Street,
Coopers Plains,
Brisbane, Queensland 4108
UK
London
85 Great Portland Street, First
Floor, London, W1W 7LT
Canada
Burlington
5096 South Service Rd,
ON Burlington, L7l 4X4
Let’s Transform Your Idea into
Reality. Get in Touch