Securing the Internet of Things (IoT): Challenges and Solutions
.jpg)
The Internet of Things (IoT) is rapidly transforming the world we live in, with the number of connected devices globally expected to reach 75.44 billion by 2025. This interconnected web of devices, from smart thermostats and wearables to industrial sensors and connected vehicles, is fundamentally reshaping how we live, work, and interact with the world around us.
In homes, IoT devices automate daily tasks, enhance comfort, and offer improved energy efficiency. Industries are utilizing IoT development services for real-time monitoring, predictive maintenance, and optimized operations. Cities are deploying smart infrastructure for intelligent traffic management and environmental monitoring. The potential benefits are many, yet there is a growing concern with this rapidly expanding network of interconnected devices - their security.
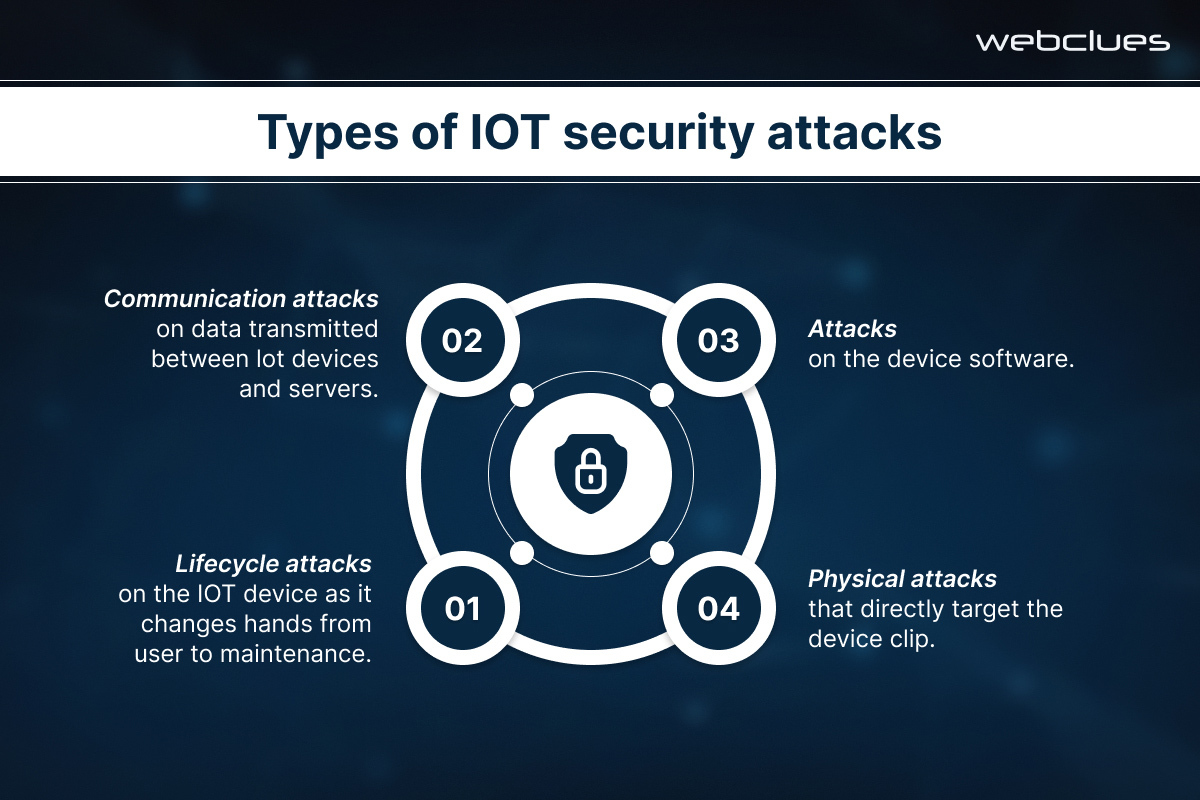
The sheer volume and diversity of IoT devices introduce unique challenges in keeping this complex ecosystem secure. Traditional security measures designed for computers and smartphones may not be sufficient for resource-constrained devices with limited processing power and often weaker authentication protocols. To retain and harness the convenience and efficiency offered by IoT devices, it is essential to implement efficient security measures, such as encryption, secure authentication, and regular software updates. This way, organizations can protect their IoT devices and the sensitive data they collect and transmit.
Challenges in Securing the IoT Ecosystem
The Internet of Things (IoT) ecosystem is a vast and complex domain, presenting a multitude of security challenges that must be addressed to maintain and improve the safety and integrity of connected devices and the data they handle.
Heterogeneity and Legacy Systems
One of the defining characteristics of the IoT ecosystem is its extensive diversity. Unlike traditional IT environments with standardized platforms and protocols, IoT comprises a myriad of devices from countless manufacturers. Each device may operate on a different operating system, utilize unique communication protocols, and have varying security features. This heterogeneity makes it extremely difficult to implement uniform security standards across the board.
Furthermore, the presence of legacy systems – older devices still in operation - poses a considerable security risk. These outdated systems often have inherent vulnerabilities due to a lack of security updates and may be incompatible with modern security solutions.
Resource-Constrained Devices
Many IoT devices, particularly those designed for low-power applications, have limited processing power and memory. This presents a significant challenge for implementing efficient security protocols. Complex encryption algorithms, for instance, can be too computationally intensive for these devices, obstructing their ability to effectively protect sensitive data. The limited resources also restrict the implementation of advanced security features like firewalls and intrusion detection systems, leaving these devices more susceptible to attacks.
Unsecured Communication Channels
Data security depends on the protection of information as it travels between devices and servers. Unfortunately, many IoT devices transmit data unencrypted across networks. This lack of encryption exposes sensitive information, such as user credentials, sensor readings, and control commands, to potential interception by attackers. Once intercepted, this data can be manipulated or used for malicious purposes, compromising the entire system's integrity.
Lack of Secure Boot and Firmware Updates
The security of any device depends heavily on its firmware, the underlying software that controls its functionality. However, many IoT devices lack secure boot processes, making them vulnerable to attacks that target the boot sequence and inject malicious code. Moreover, the absence of automated firmware update mechanisms leaves these devices exposed to newly discovered vulnerabilities that can be exploited by attackers. This lack of secure boot and timely updates creates a window of opportunity for attackers to gain unauthorized access and control over devices.
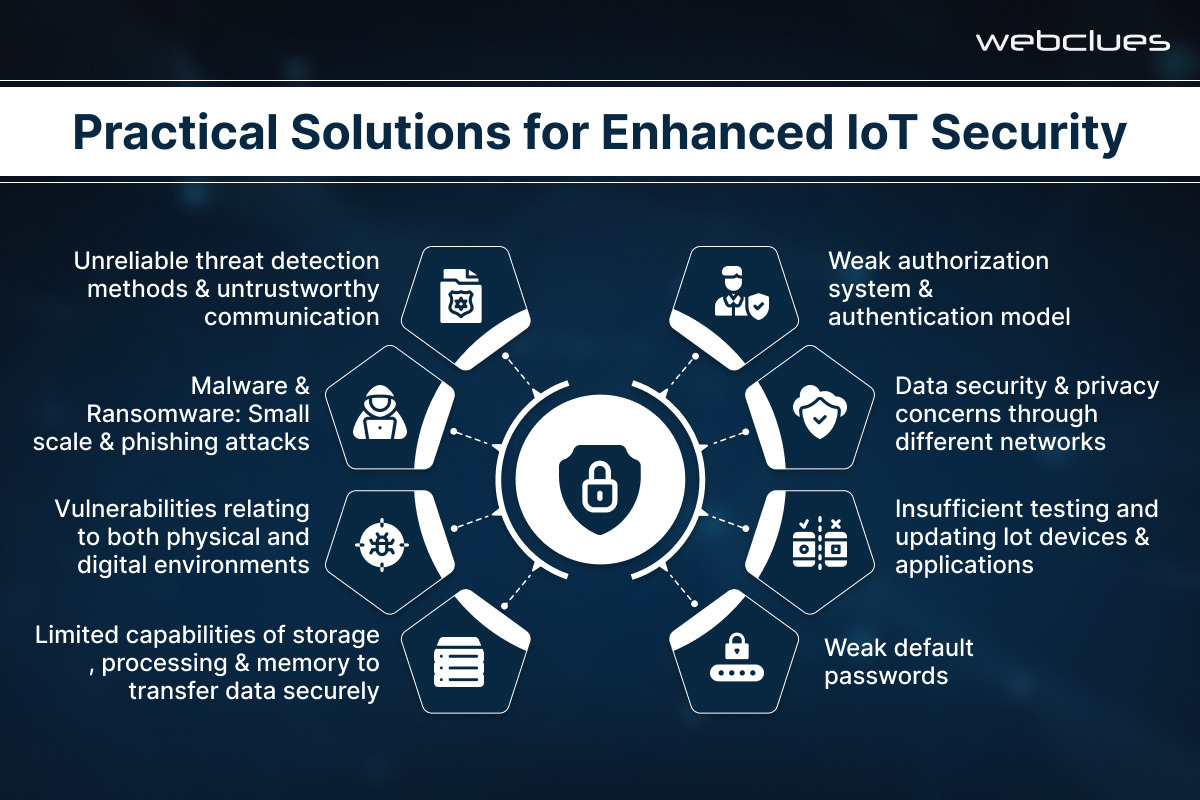
Practical Solutions for Enhanced IoT Security
The security challenges within the IoT space are significant but not insurmountable. By implementing a multi-layered approach that prioritizes security throughout the development lifecycle and utilizes effective solutions, we can build more secure interconnected devices.
Secure by Design Principles
Prioritizing security throughout the entire development lifecycle of IoT devices is essential to eliminate risks and vulnerabilities. Secure by design principles involve incorporating security measures from the ground up, including secure coding practices, regular security audits, and vulnerability assessments. By adopting a security-first mindset, IoT manufacturers can create devices that are inherently more resilient to attacks and better equipped to protect sensitive data.
Robust Authentication and Access Control
Implementing strong authentication mechanisms and granular access controls is crucial to prevent unauthorized access to IoT devices and the networks they operate in. Multi-factor authentication, which combines two or more authentication factors (e.g., password, biometrics, or hardware tokens), adds an extra layer of security and makes it harder for attackers to gain access. Role-based access controls (RBAC) allow organizations to define and enforce access policies based on the user's role, ensuring that each user has only the necessary permissions to perform their tasks.
Encryption Throughout the Stack
Data encryption scrambles information into an unreadable format, rendering it useless to unauthorized parties. Implementing encryption "throughout the stack" makes sure that data remains protected at all stages:
- Encryption at Rest: This protects data stored on devices in case of physical breaches.
- Encryption in Transit: This protects data as it travels between devices and servers, preventing eavesdropping.
- Encryption in Use: This ensures data remains encrypted even while being processed by the device, minimizing the vulnerability window.
Patch Management and Secure Updates
Proactively addressing vulnerabilities through automated and secure firmware update mechanisms is crucial to maintaining the security of IoT devices. Patch management processes should include regular vulnerability assessments, timely deployment of security patches, and efficient update mechanisms. Automated firmware updates help organizations keep their IoT devices up-to-date with the latest security fixes, reducing the attack surface and minimizing the risk of exploitation. Secure update processes, such as code signing and firmware integrity checks allow only authentic and authorized updates to be installed on IoT devices.
Tapping into Emerging Technologies
Advancements in emerging technologies offer promising solutions for improving IoT security. Hardware-based security modules, such as Trusted Platform Modules (TPMs) and Secure Elements (SEs), provide hardware-based protection for cryptographic keys and sensitive data. Blockchain technology can be utilized for secure data provenance, facilitating the integrity and traceability of IoT data. Post-quantum cryptography algorithms, which are resistant to attacks by quantum computers, can future-proof IoT systems against evolving threats. By adopting these emerging technologies, organizations can stay ahead of the curve and build a more resilient IoT ecosystem.
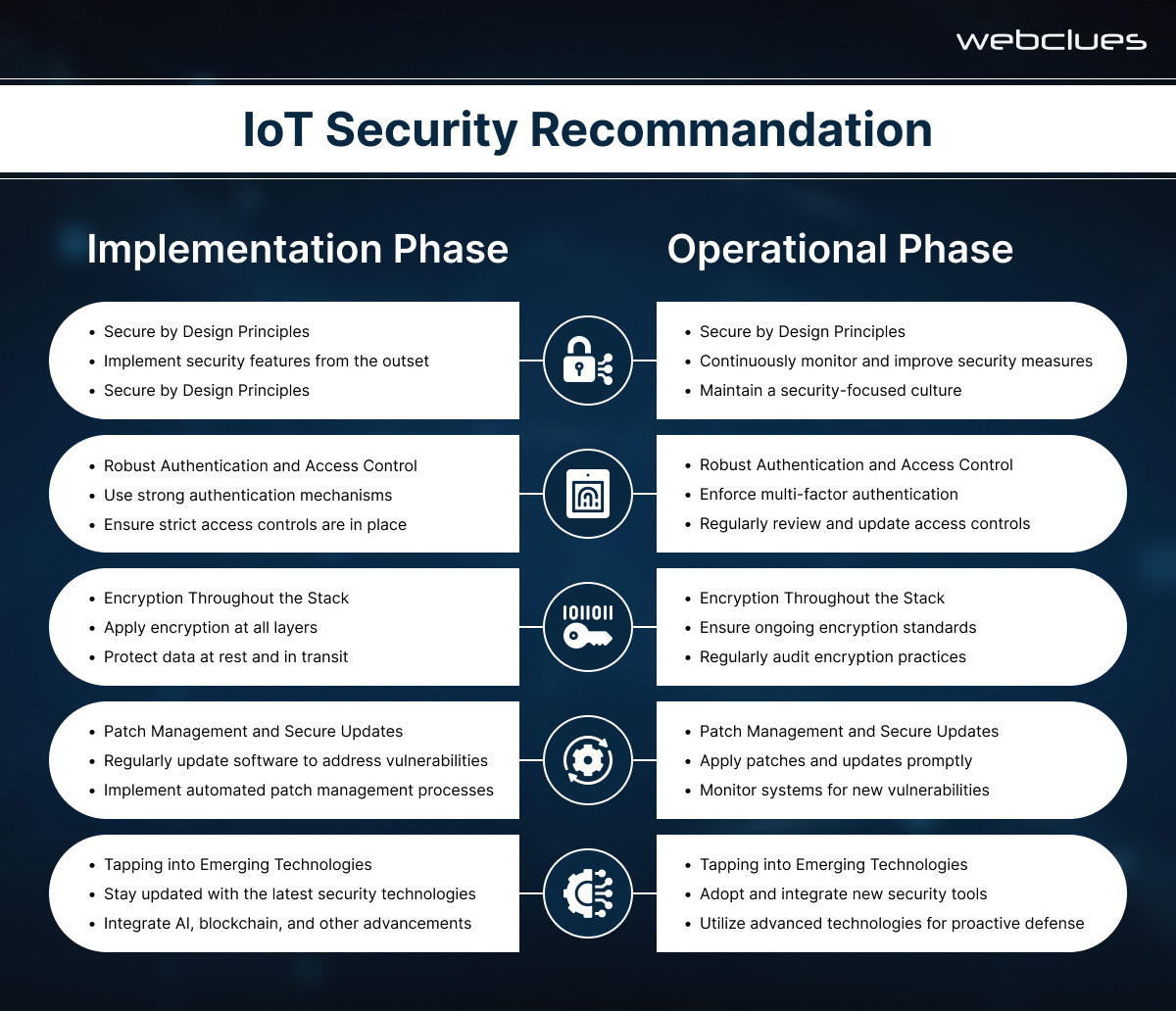
A Holistic Approach to IoT Security
While technological solutions are essential for securing the Internet of Things, a truly comprehensive approach to IoT security requires a holistic perspective that is not limited to just the technical aspects.
Shared Responsibility Model
Securing the vast and interconnected web of IoT devices requires a collaborative effort. The "Shared Responsibility Model" emphasizes that the responsibility for security doesn't solely lie with manufacturers or software developers.
It's a collective effort that requires:
- Manufacturers to prioritize secure design principles, implement secure coding practices, and provide regular firmware updates.
- Hiring IoT Developers to create secure applications that adhere to best practices and minimize vulnerabilities.
- End-Users to adopt secure practices like using strong passwords, utilizing multi-factor authentication where available, and keeping software updated on all connected devices.
Security Awareness and User Education
Educating end-users on secure practices is vital for the overall security of the IoT ecosystem. Many IoT security breaches occur due to user negligence, such as using default or weak passwords, failing to update devices, or inadvertently granting unauthorized access. By raising security awareness and providing user-friendly guidance on security best practices, organizations can allow end-users to be active participants in securing their IoT devices and the data they generate.
Standardization and Regulations
The lack of industry-wide security standards and regulations has been a substantial challenge in the IoT domain. Establishing common security frameworks and guidelines can help create a baseline level of security for all IoT devices, regardless of the manufacturer or platform. Governments and regulatory bodies play a crucial role in developing and enforcing such standards, making sure that IoT devices meet minimum security requirements before being deployed in the market.
The Security-Conscious Future of IoT
The incredible potential of IoT depends on the fundamental principle of trust. As we integrate more devices into our homes, businesses, and critical infrastructure, efficient security measures become crucial. By prioritizing security throughout the entire lifecycle of IoT devices – from design to deployment – we can cultivate a future where trust underpins every interaction within the interconnected environment.
At WebClues Infotech, we are an IoT development company that harnesses advanced security solutions and industry best practices to design, develop, and implement secure IoT solutions for our clients. We understand the unique challenges of securing diverse IoT ecosystems and work collaboratively to build trust through robust security architecture.
If you're ready to take the first step towards a more secure IoT future, contact us today to schedule a consultation and learn how we can help you build trust in the Internet of Things.
Build Your Agile Team
Hire Skilled Developer From Us
Mitigate security risks in your IoT deployments with our expert solutions
Partner with WebClues to build a secure foundation for your IoT projects. Our industry-leading solutions minimize security risks and safeguard sensitive data, allowing you to focus on maximizing the potential of your connected devices.
Connect Now!Our Recent Blogs
Sharing knowledge helps us grow, stay motivated and stay on-track with frontier technological and design concepts. Developers and business innovators, customers and employees - our events are all about you.
Contact Information
Let’s Transform Your Idea into Reality - Get in Touch
India
Ahmedabad
1007-1010, Signature-1,
S.G.Highway, Makarba,
Ahmedabad, Gujarat - 380051
Rajkot
1308 - The Spire, 150 Feet Ring Rd,
Manharpura 1, Madhapar, Rajkot, Gujarat - 360007
UAE
Dubai
Dubai Silicon Oasis, DDP,
Building A1, Dubai, UAE
USA
Delaware
8 The Green, Dover DE, 19901, USA
New Jersey
513 Baldwin Ave, Jersey City,
NJ 07306, USA
California
4701 Patrick Henry Dr. Building
26 Santa Clara, California 95054
Australia
Queensland
120 Highgate Street, Coopers Plains, Brisbane, Queensland 4108
UK
London
85 Great Portland Street, First
Floor, London, W1W 7LT
Canada
Burlington
5096 South Service Rd,
ON Burlington, L7l 4X4